MBTA Cryptography Security Analysis
Spring 2008
During the Spring of 2008 I worked with three other students to analyze the security of the Boston transit fare collection system. The research was conducted in the MIT Computer and Network Security course 6.857. After several weeks of reverse-engineering, software development, testing, and analysis, we found several major security holes in the MBTA fare collection system. We discovered significant issues with the magnetic card media, the RFID fare cards, and the physical security of the system. We discovered several exploits that would allow one to generate arbitrary value fare cards for zero cost. In addition, we developed several low cost software-only solutions to fix the security holes for the MBTA. Our initial offer to assist the transit agency in fixing the security holes was initially poorly received, but later they agreed to accept our offer to assist and allow us to assist in patching the vulnerabilities we discovered.
Analyzing the CharlieTicket
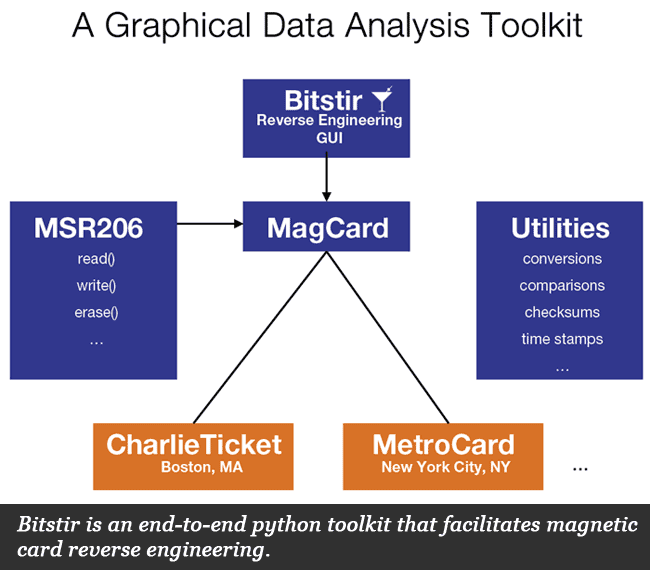
We discovered that instead of using an account system with value stored in a central location, the fare collection system stores value on the actual fare card. To reverse engineer the data format on the cards, we purchased several hundred dollars worth of magnetic fare cards to look for patterns in the data. Looking at binary data, these patterns were extremely difficult to see without help, so we wrote a Python code-breaking toolkit called Bitstir that assisted in comparing cards, visually analyzing data, testing hypotheses, and performing various mathematical transformations.
Custom Code Breaking Software Suite: Bitstir is a toolkit we developed to perform computational analysis of the magnetic media.
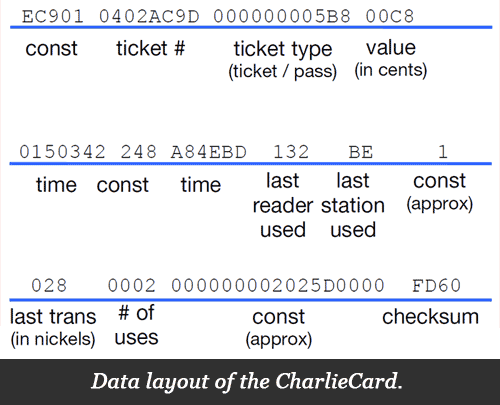
With our large body of data (stacks of purchased magnetic fare cards) and powerful reverse-engineering software (Bitstir), we were able to decode the layout of the CharlieTicket magnetic media, reverse engineer their encryption, and discover implementation flaws in how the encryption was implemented. The figure below illustrates the layout of data on the card. With the data location, encoding, and security mechanisms known, we were able to generate unique ID number arbitrary fare cards worth hundreds of dollars.
Simplified summary of the CharlieTicket encoding.
Analyzing the CharlieCard
Once we discovered how to compromise the magnetic media system, we investigated to see if the RFID payment system was also vulnerable. The RFID payment card, called the CharlieCard, is based on the Mifare Classic standard. Building on top of the research conducted by Karsten Nohl, et al, we uncovered several ways to discover the secret key that allows wireless reading and writing of CharlieCards. Once we discovered the secret key, cards could be read and remotely cloned from someone's pocket without their knowledge (requires close proximity).
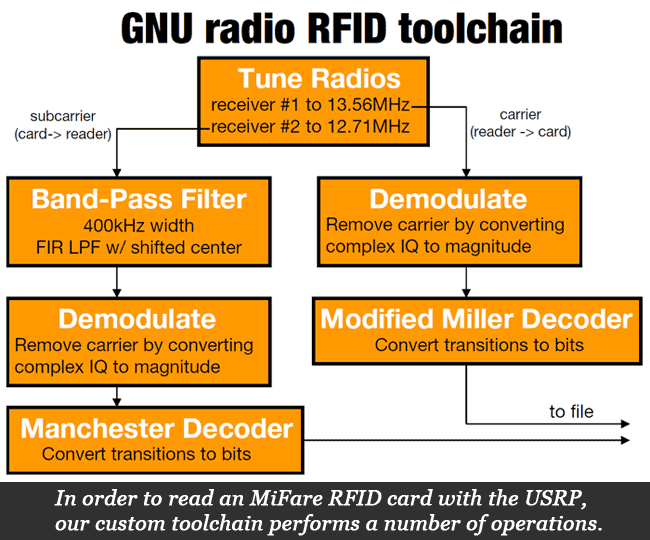
Since we needed to conduct low-level analysis of the RFID card transmission, we used a software radio hardware platform called the USRP along with the open-source software radio toolkit GNU Radio. After bandpass filtering for the correct upstream and downstream frequencies, the signals we read are seen in the figure below.
The data is encoded and transmitted on a sinusoidal carrier. In order to convert this wave into the challenge/response pairs from the Mifare card and the subsequent encrypted transmission, we wrote a software plugin for GNU Radio to read Mifare RFID cards. The figure below demonstrates the blocks to this plugin that are required before valid data comes out. Using this custom toolchain, we were able to read the data transmission between the payment card and turnstile, and then analyze the data.
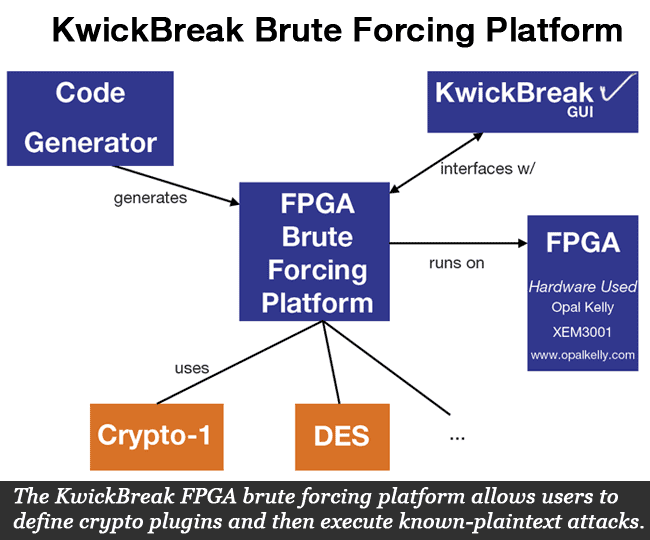
There are several attacks that can be executed on the Mifare card. An excellent overview on these attacks and how the encryption algorithm used by the Mifare card (Crypto-1) works can be found in this paper. The attacks exploit weaknesses in the Crypto-1 cipher, and allow the 48-bit key space to be reduced. To exploit the power of massively parallel computing, we designed and wrote a Verilog FPGA implementation of a generalized known-plaintext attack brute-forcing utility that supports several cryptography algorithm plugins. Using the Crypto-1 plugin, it can quickly brute force a sniffed transaction to recover the secret key. The figure below demonstrates the Kwickbreak FPGA brute forcing framework we wrote. The second figure shows the user-friendly interface and the attachment to a USB FPGA board.
The Aftermath
Our research made international media in both academic and general publications. The subsequent federal lawsuit against us (which was rejected by the court) also established important US precedent on First Amendment protections with respect to the CFAA. Here are a few of the domestic publications and television networks that covered our findings: